Naval Postgraduate School
Events
Global Climate and Energy Policy Trends – 2024 and Beyond
ME Auditorium, Bldg #255
12:00 to 12:50 p.m.
The Naval Postgraduate School offers graduate programs, masters and PhDs, both on and off campus and Distance Learning, through our academic departments.
NPS offers world-class graduate degree programs in a wide variety of disciplines to eligible U.S. military students, international students, DoD civilian employees, and a limited number of defense contractors.

NPS research centers, institutes and Academic Groups deliver defense solutions and develop interdisciplinary expertise across the university's applied research and education programs.
NPS Online provides defense-focused education through tailored and accessible graduate-level online and on-location learning opportunities.
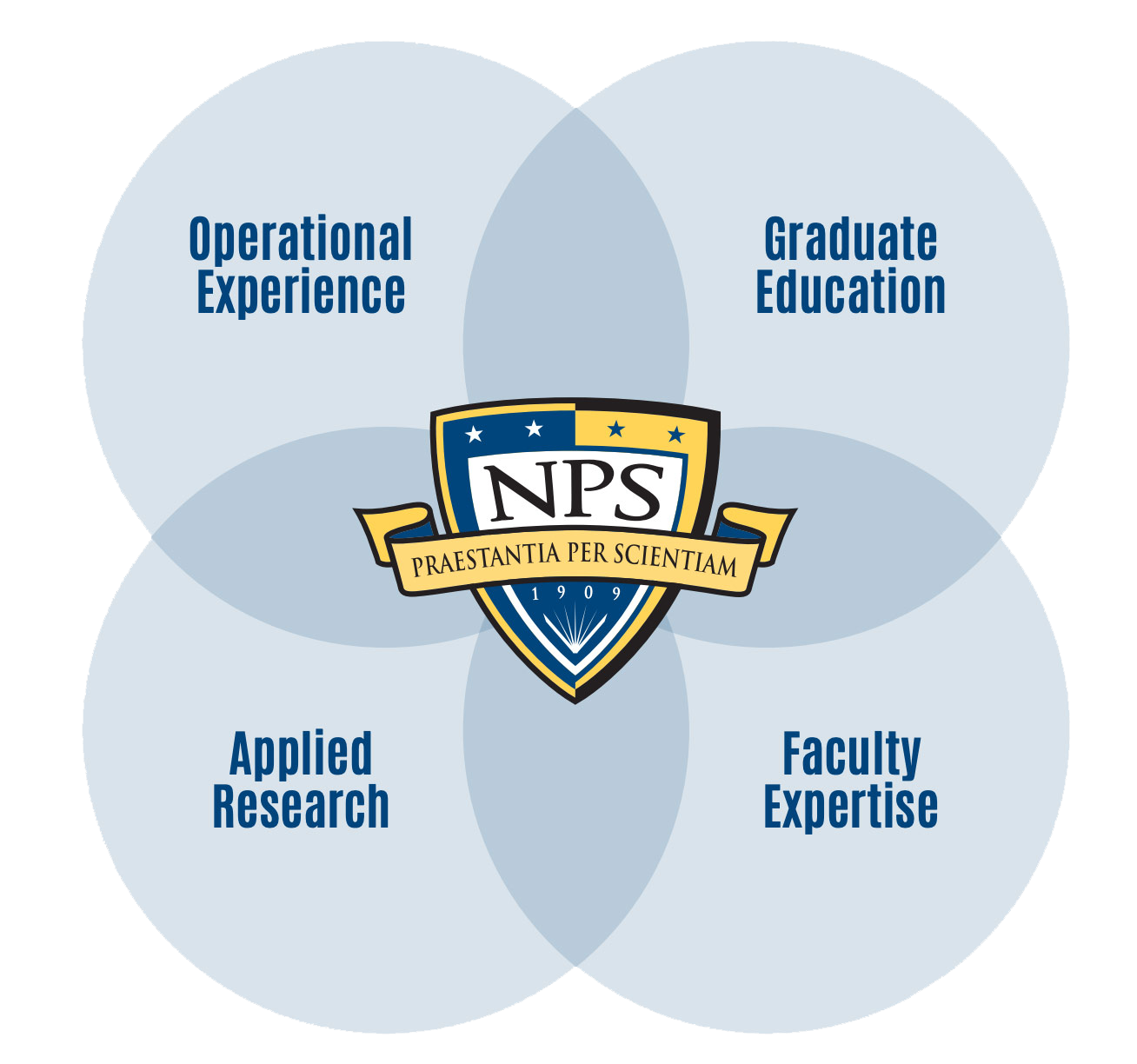
THE NPS DIFFERENCE
Only NPS synchronizes student operational experience and graduate education with applied research and faculty expertise to deliver innovative warfighting solutions and leaders educated to employ them. Learn more.

Welcome to the official YouTube channel for the Naval Postgraduate School in Monterey, California. For more information about the university, its unique mission and academic programs, visit NPS on the web at http://www.nps.edu.
Naval Postgraduate School
Higher Education
1001-5000 employees
The Naval Postgraduate School (NPS) provided post-baccalaureate education to military officers and other members of the United States defense and national security community. The mission of NPS is to provide high-quality, relevant and unique advanced education and research programs that increase the combat effectiveness of the Naval Services, other Armed Forces of the U.S. and our partners, to enhance our national security.
View more on https://www.linkedin.com/school/nps-monterey/
Official Instagram page of NPS, a graduate research university offering advanced degrees to the U.S. Armed Forces, DOD civilians and int'l partners.
https://www.instagram.com/nps_monterey/
ALUMNI SPOTLIGHT

"NPS is the flagship technical graduate school for the Navy and DOD," Paparo said. "This school is ruthlessly focused on warfighting, and in the geography that is the hub of technical innovation in the world."
~ Commander, U.S. Pacific Fleet, Adm. Samuel Paparo, a graduate of NPS' Systems Analysis program
Find guidance on COVID-19 mitigation measures see the NPS Safety Office COVID-19 page with links for up-to-date command/DoD guidance and COVID FAQs. For status of base and services see NSAM homepage.
The NPS Annual Report highlights the university's major achievements and initiatives throughout the course of the calendar year.
NPS faculty are world-renowned experts in a broad range of critical disciplines. Search the university’s directory of faculty experts.