Crowd Modeling Group - The Crowd Dynamics Modeling Group
The Crowd Dynamics Modeling Group at NPS is a cross-disciplinary group of academics studying and modeling the way crowds interact with security forces. Our group includes experts in psychology, sociology, simulation, data farming, and data analysis. Our focus is on advancing understanding of how crowds behave, particularly in response to security force activities, in order to develop informed rules of engagement for use of intermediate force capabilities weapons. These Intermediate Force Capabilities (IFCs) provide a range of non-lethal and less-lethal options.
We have developed a prototype agent-based simulation model for crowd-security force interactions for use in scenarios such as protest events, border control, and humanitarian aid distribution. We seek to make our model match reality as closely as possible in order to obtain effective policies that achieve their intended results. Thus, unlike most models, ours incorporates a broad range of detailed, in-depth insights of social science. We use social science insights and conclusions on individual motivations, individual responses to others and situations, group dynamics, crowd behavior, how identity affects individuals and groups, and how people respond to security force tactics. Our model includes a nuanced view of emotions and emotional contagion, reflecting the state of the literature on anger, fear, and a number of other emotions. Our model also explicitly incorporates static and dynamic aspects of identity, especially social identity dynamics, that have been seen to play in important role in potentially hostile crowd behavior.
Workbench for refining Rules of Engagement against Crowd Hostiles
The Workbench for refining Rules of Engagement against Crowd Hostiles (WRENCH) simulation has been constructed for the purpose of better understanding the effects of social identity dynamics on crowd behavior, particularly in situations where security forces are active in patrolling or securing an environment in which crowds may form and become hostile. The initial application of WRENCH is to address questions regarding the use of intermediate force capabilities (non-lethal) weapons, particularly addressing weapon selection and rules of engagement. The goal is to effectively deescalate potentially violent situations while maintaining force legitimacy. In terms of the PEMSII-PT framework, WRENCH explicitly models the Military, Social, Physical, and Time aspects.
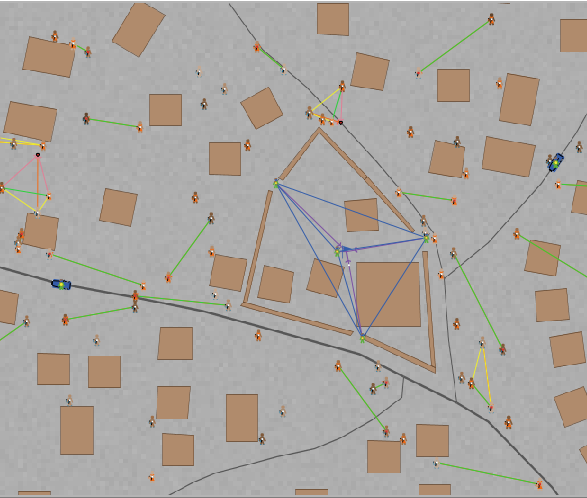
WRENCH is constructed as a stochastic agent-based simulation model in NetLogo, and is essentially a complex adaptive system. It is a bottom-up model, where each agent’s internal construction determines its responses to interactions with other agents and changes in the environment. WRENCH is the result of several years of development by the Naval Postgraduate School, and further development of the software continues. A typical model within WRENCH covers a specific geographic area of less than one square mile and includes detailed geographic features such as roads and buildings from GIS data uploaded into WRENCH. (WRENCH is capable of modeling larger geographic areas though.) Each individual person and security force member is modeled in detail, including having its own demographic characteristics, emotions, needs, experiences, perceptions, intentions, behaviors, and potential social identity group (SIG) identification. Each SIG is modeled as having constituents, needs, and intentions, and potentially a higher level group identification as well. The timeframe is typically very focused, tracking crowd and force activities over hours-to-days with time-steps usually being one second.
A typical WRENCH scenario includes a variety of people with different objectives moving about a specific geographic area while security forces maintain the security of the area. People who have increasing anger, unmet needs, or hostile intentions may develop hostile behavior toward the forces. Once a crowd begins to form and demonstrates hostile behavior, the forces engage the crowd according to the user-specified rules of engagement for the scenario, utilizing the user-specified IFC weapon options for the scenario. When crowd hostilities have abated, security forces resume their default behavior for maintaining security of the area.
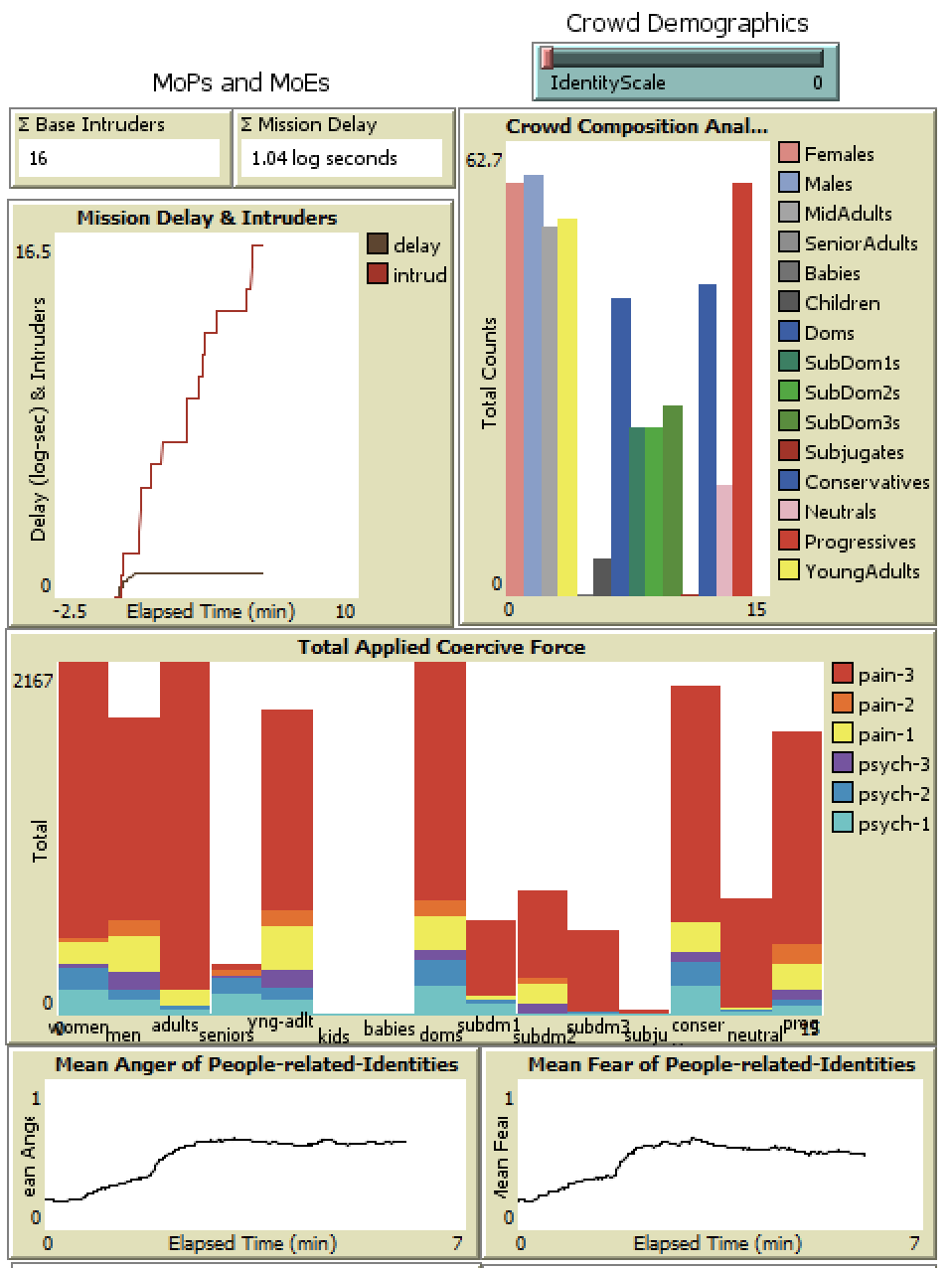
WRENCH is capable of outputting a wide variety of information about each run. Some metrics of particular interest are the changes in the population’s overall anger, fear, hostility levels, and beliefs about security force legitimacy, along with the amount and types of force the security forces used to manage crowd hostilities.
WRENCH development has been funded primarily by the Joint Intermediate Force Capabilities office (https://jnlwp.defense.gov/) and also by the U.S. Army Training and Doctrine Command (https://www.tradoc.army.mil).
Our History
Our crowd model began with the early team’s Social Resiliency Model (SoReM), which was focused on the question of ‘social resiliency.’ Analysis of the responses by organizations that successfully adapted to seemingly existential threats led to our emphasis on social identities and those identities’ relationships to individuals. Our conclusions indicated that individuals hold both their own identities and those of a social identity group with multiple influences on behavior. This would prove a key insight in deciphering the behavior of individuals in crowds, steering our analysis on a path distinct from either a mob mentality approach or a self-centered individual rationality emphasis.
Social Resiliency was broadly understood as the capability of a social organization to undergo perceived and actual threat to its existence while continuing to function with minimized disruption. Even in these early incubatory stages we recognized that truly resilient social organizations were more ‘adaptive’ in their responses, to existential or sense-making crises than was being characterized in the academic literature. SoReM represented one of the very early attempts to expand and formalize our understanding of the nature of the resilient adaptation of social organizations to crises.
Among the critical early insights generated by the SoReM Initiative was that resilient social organizations were invariably distinguished by their ability to maintain what became known as multi-scale social identities. In addition, we realized that the critical coherency-generating strategy employed by any given social identity within the organization was both relatively independent of other identities within the organization and naturally inclined to oscillate between two distinct and largely independent coherency-generating strategies (at a rate that correlated with scale).
What appeared to be the primary source of adaptability in these resilient organizations was their ability to flexibly and expeditiously orchestrate the proportional distribution of available resources to their various constituent social identities and the nature of the coherency-generating strategies employed by the various social identities both above and below the engaging identities. These realizations, along with the complex interactions and feedbacks they implied, soon precipitated a shared conviction that a modeling framework would be required to support any systematic search for a theory of optimal resiliency management. SoReM, the computational framework, was born from these perceived requirements. Much can be and has been said of the insights that flowed from both the construction and the use of the SoReM framework. Suffice it to point out two significant challenges faced by the early investigators: First, the tendency of ‘existential threats’ to disrupt shared narrative-based sense-making processes was soon identified as problematic for any rational-choice modeling approach; resilient organizations simply weren’t managing these identity dynamic processes through some traditional economic choice process, whether ‘Kahneman and Tversky’-like or otherwise. Second, the two primary oscillating modes of social coherency generation were soon recognized as being, for the constituents of an identity, not just different and unfamiliar but actively the source of a collectively shared aversion (a hysteresis effect if you will). Social identities clearly resist changing their coherency generating strategy, even when it is unambiguously in their interest to do so; and it is this resistance that, importantly, the resilient organization must be able to manage/ overcome. How they manage to do so was one of the critical research questions in those early days.