Events - Global ECCO
Global ECCO presents: CTX Conversations, Waves of Valor: Discussing the Legacy of the Navy SEALs and Beyond
Join us for the next CTX Conversations event, "Waves of Valor: Discussing the Legacy of the Navy SEALs and Beyond." This hybrid event will take place on August 8 at 12 PM, both in person at NPS in Glasgow 109 and online via Zoom. Our distinguished speakers include NPS professor Dr. Tommy Jamison and Mr. Ben Milligan, author of By Water Beneath the Walls, a history of Special Forces. Don't miss this insightful discussion!
NOTE: The views presented are theirs alone and do not necessarily represent the views of DoD or its components.
CTX Conversations | Waves of Valor: Discussing the Legacy of the Navy Seals and Beyond
Date: August 8 @ 12PM PDT
Location: Glasgow 109
Zoom ID:
https://nps-edu.zoomgov.com/j/1618955024
Passcode: Ecco123$$$

Global ECCO Presents: CTX Conversations, The Future of Insurgencies and Radical Groups in Africa, with Dr. Timothy Jones in a discussion with Dr. Christopher Anzalone
As part of our commitment to fostering dynamic dialogue and collaboration, we invite you to join us for CTX Conversations—an ongoing series of virtual discussions covering a spectrum of critical topics. From irregular warfare to counterterrorism and East Asian security, these conversations provide a platform for experts worldwide to share insights and perspectives with a live online audience.
Stay tuned for more information on the upcoming CTX Conversation, 9 July at noon Pacific Daylight time, which will feature Dr. Timothy Jones in a discussion with Dr. Christopher Anzalone on the status, activities, and possible future plans of radical insurgent groups such as al Shabaab on the African continent.
Don't miss this opportunity to gain valuable insights from leading experts in the field.
NOTE: The views presented are theirs alone and do not necessarily represent the views of DOD or its components.
CTX Conversations | The Future of Insurgencies and Radical Groups in Africa
Date: July 9 @ 12PM PDT
Zoom: https://nps-edu.zoomgov.com/j/1607036811
Passcode: CTXcon&m$1

Global ECCO Presents: CTX Conversations, The Ukraine War: Military Lessons and Prospects for Peace
We invite you to join us for this year's second CTX Conversation on May 29 at 1200 PDT via Zoom, featuring a discussion between Dr. John Arquilla and Dr. Katya Drozdova, a distinguished professor of Business, Information Systems, and Political Science at Seattle Pacific University's School of Business, Government, and Economics.
Prof. Drozdova has an extensive background in research and has lectured at various defense, policy, and educational institutions. She has also taught a wide array of courses, including Cyberpower and Cybersecurity, Counterterrorism, International Relations, Information Systems, Research Methods, Strategy, and Economics.
During the conversation, Dr. Drozdova and Dr. Arquilla will delve into the causes and conduct of the war, the interplay between traditional tactics and modern technologies on the battlefield, the risks of escalation, and the potential for reaching a negotiated resolution to the conflict.
NOTE: The views presented are theirs alone and do not necessarily represent the views of DOD or its components.
CTX Conversations | The Ukraine War: Military Lessons and Prospects for Peace
Date: 29 May @ 1200 PDT
https://nps-edu.zoomgov.com/j/1606515835
Passcode: .yKzi6k#=P

Global ECCO Presents: CTX Conversations with Mr. Thomas Friedman - Strategic Implications of the Gaza War
The Combating Threats Exchange Journal (CTX) announces the launch of CTX Conversations, a series of virtual discussions between recognized area experts from around the world, covering a spectrum of critical topics, including irregular warfare, counterterrorism, East Asian security, and much more.
We are honored to kick off this series with Dr. John Arquilla, Distinguished Professor Emeritus at the Naval Postgraduate School, in conversation with Pulitzer Prize winning author and journalist, Thomas Friedman. Together, they will delve into the strategic implications of the ongoing conflict in Gaza, offering their own insights and analysis on this difficult topic.
Mark your calendars for March 15, 2024, at 12 PM PST to join us for this thought-provoking session. Following the discussion, there will be an opportunity for audience members to ask questions and share their own thoughts with Mr. Friedman, Dr. Arquilla, and the rest of the online audience. Don't miss out on this rare opportunity.
If you are interested in attending this virtual discussion, please contact Amina Kator-Mubarez at akatormu@nps.edu.

JSOU - SOCbT Course
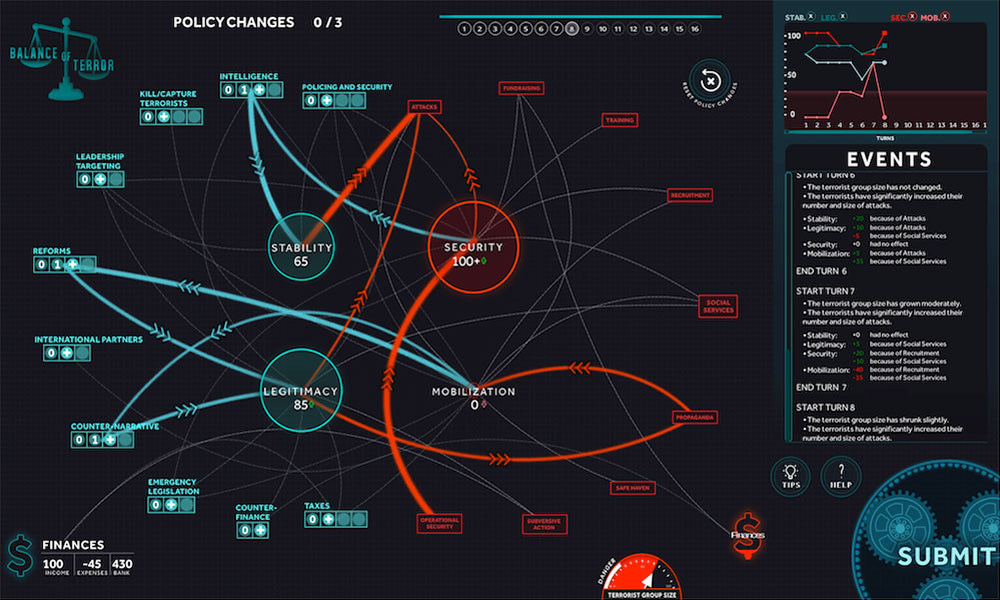
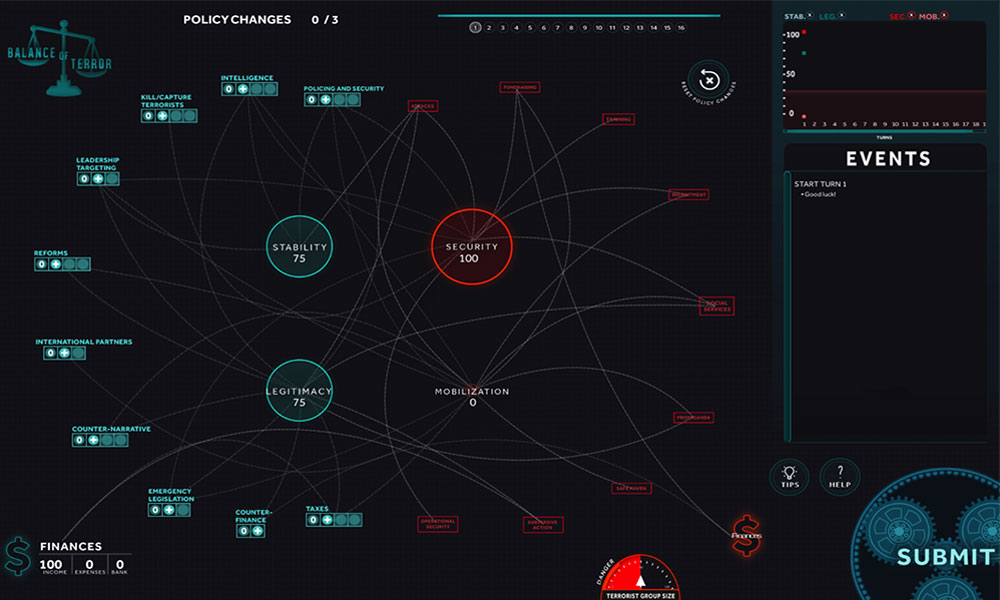
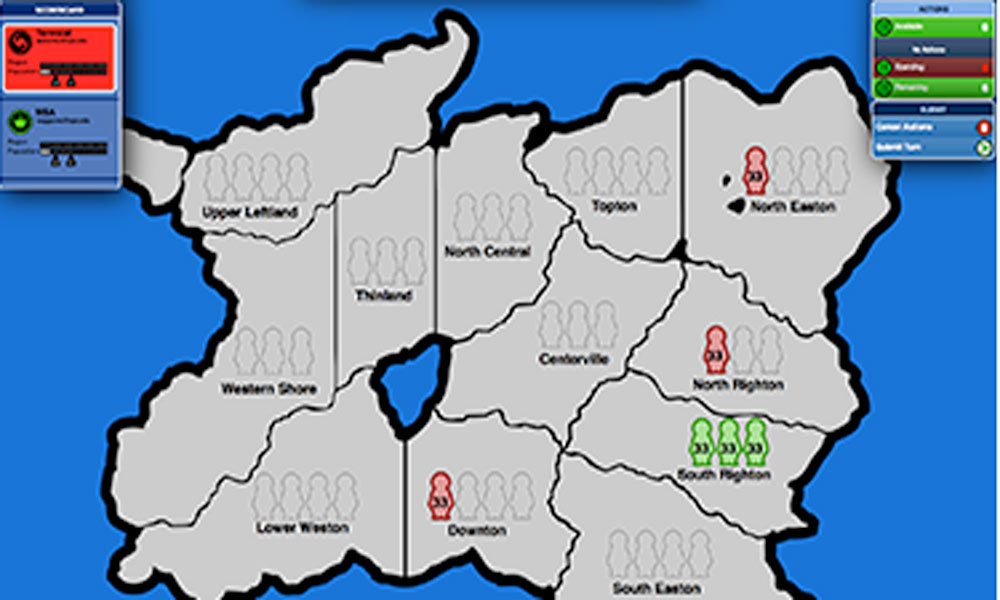
The Global ECCO team will be facilitating Balance of Terror, a two-player strategy game focused on terrorism and counterterrorism, at JSOU.
JSOU - CVE Course
The Global ECCO team will be facilitating Contagion, a two-player strategy game focused how terrorists spread their ideologies and how states counter that with their own ideologies.
Strategic Gaming Facilitation: Dark Networks — CORE - SNA
Strategic Gaming Facilitation: Dark Networks — DIA

Strategic Gaming Facilitation: SOCbT — JSOU
Strategic Gaming Facilitation: Dark Networks — JSOU
Strategic Gaming Facilitation: Dark Networks — JSOU

Strategic Gaming Facilitation: Dark Networks — DIA

Strategic Gaming Facilitation: Dark Networks — Peruvian War College and CORE Lab (NPS)
Members of the CORE lab from the Naval Postgraduate School will be facilitating the game, Dark Networks, for the course titled, "Trust, Intelligence, and Networks" at the Peruvian War College.
This course examines the basic principles of trust and influence, especially as they relate to social networks. Students will acquire a theoretical foundation for these concepts and how they apply to a broad spectrum of areas. The course also introduces the basic concepts discussed in the class—trust, influence, and social networks—and how they are interrelated as well as explores various ways that trust, influence, and networks play themselves out in different aspects of life and irregular warfare, such as small groups, military teams, social movements, dark networks, and so on.
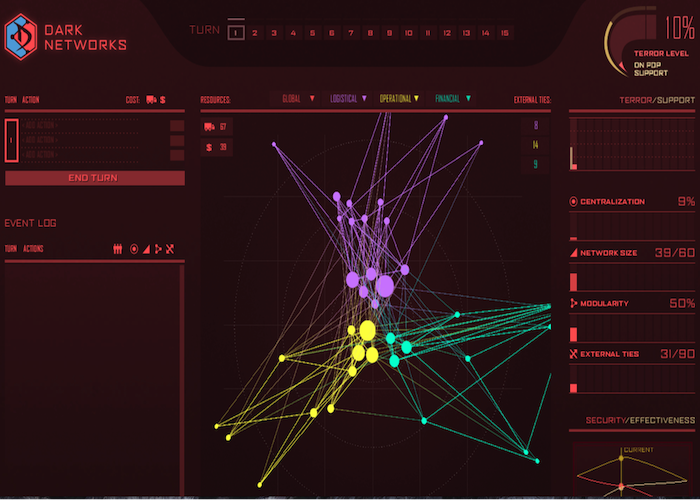
The Dark Networks game focuses on the organizational structure of terrorist groups and how these structures can be altered to make the terrorist group more or less effective. It reinforces many of the concepts and ideas from the field of social network analysis (SNA). It is a two-player, strategic game between the state and the terrorist. Each player may have a strategy to defeat the other, but they must adapt their strategies over time to maximize their advantages. The core tradeoff in this game is between security and effectiveness for the terrorist group. Measures taken to increase effectiveness (growing, centralizing) will diminish the terrorist group's security, and vice versa. This forces players to think about which attribute (security or effectiveness) they wish to maximize. This will change depending on the timing in the game and players' strategies.

Strategic Gaming Facilitation: Dark Networks — JSOU

Strategic Gaming Facilitation: Contagion — JSOU
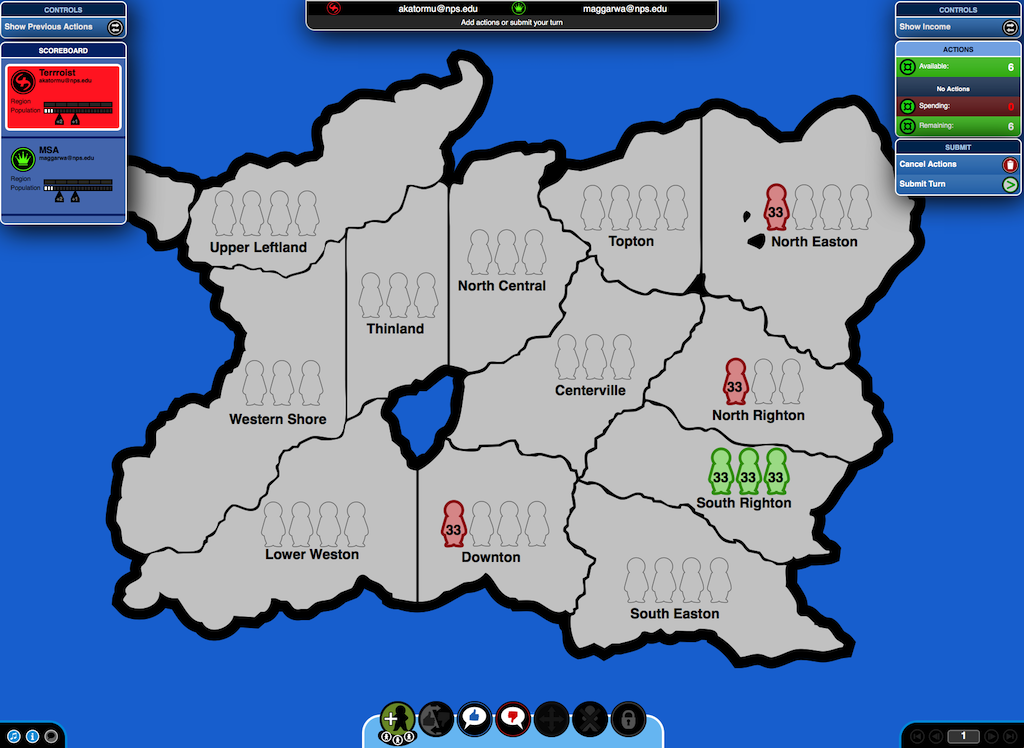
Strategic Gaming Facilitation: Contagion — FBI ILEA

Strategic Gaming Facilitation: FBI - IEP - Panama

Strategic Gaming Facilitation: Dark Networks — FBI ILEA

Strategic Gaming Facilitation: Dark Networks — FBI ILEA

Panel Session - Afghanistan: Reactions and Reflections

Strategic Gaming Facilitation: CyberStrike — Naval Postgraduate School
The ECCO team will help Professor Deborah Gibbons facilitate the Global ECCO strategic game, CyberStrike, for her class, "Management of Teams."
The MoT course examines the differences between groups and teams, between leader-managed and self-managed teams, between virtual and face-to-face teams, and between effective and ineffective teams. Analysis of effective teams include such issues as team dynamics, decision making, rewards, commitment, and the management of conflict (inter-personal, intra-team, and inter-team) in which power, influence and negotiation play central parts.
CyberStrike is a six-player game that simulates the complex strategic environment of cyber conflict. Players can play as criminals, terrorists, hackers, or states, with each role having different capabilities and goals. Players have to consider how their offensive capabilities match up with their adversaries’ defensive capabilities, and vice versa; whether to attack opponents or defend against them; to retaliate against attacks, particularly if the perpetrator is unknown; to invest in offense, defense, or detection capabilities; to ally with others; to share information or not; and how they can deter future attacks.
The game is intentionally designed for thinking about the macro, strategic decisions in the cyber world. It does not require or teach any technical aspects of cyber conflict.


